4-Way Handshake in 802.11 Wi-Fi
The 4-way handshake is a key process in the establishment of a secure connection between a client device and a Wi-Fi access point. It’s primarily used in WPA2-PSK (Wi-Fi Protected Access 2 with Pre-Shared Key) and WPA3-Personal security protocols. Here’s how r it works, along with an overview of the authentication and association process:
State Machine of a client joining a 802.11 AP
- Unauthenticated and Unassociated
- Authenticated and Unassociated
- Authenticated and Associated
- Exchange Keys using 4WHS
Authentication step has nothing related to security or password. It just verifies if the STA is a 802.11 STA and can talk to AP.
Authentication and Association Process:
Probe request/Response
- The client device sends a Probe Request frame to discover nearby Wi-Fi networks.
- The access point responds with a Probe Response frame, providing information about the network, including its SSID (Service Set Identifier) and supported security protocols.
Authentication
- The client sends an Authentication Request frame to the access point, indicating its intention to join the network.
- The access point responds with an Authentication Response frame. In open networks, this step is often skipped.
Association
- The client sends an Association Request frame to the access point, specifying the desired SSID and other relevant information.
- The access point responds with an Association Response frame, acknowledging the client’s request after it verifies that the client supports the required protocols to connect to the AP.
4-way Handshake
Purpose
- Key Exchange: Facilitates exchange of cryptographic keys between client and AP, which are essential for encrypted data transmission.
- Mutual Authentication: Allows both client and AP to authenticate each other’s identities.
Key Terminologies
- MSK - Master Session Key
- PMK - Pairwise Master Key
- GMK - Group Master Key
- PTK - Pairwise Transient Key
- GTK - Group Temporal Key
- MIC - Message Integrity Code
Group Keys are for Broadcast Traffic and Pairwise Keys are for Unicast Traffic.
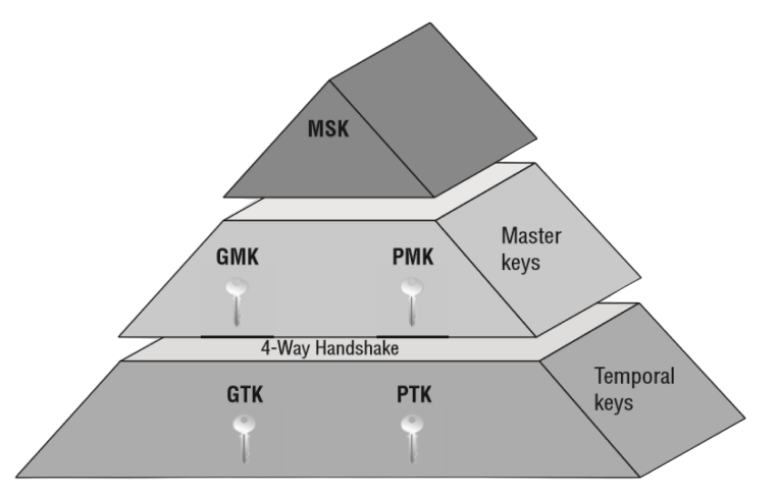
Master Keys
MSK - Master Session Key
Also known as AAA key, used to derive unique PMK for each different client in the case of enterprise networks. Enterprise networks only.
PMK - Pairwise Master Key
The pairwise master key (PMK) is a 256-bit key at the top of the key hierarchy and is used indirectly for unicast traffic and the WPA 4-way handshake. The wireless client and AP have the PMK, which should last the entire session, so it should not be exposed. So this is not used to encrypt the traffic directly. 8-63 ASCII characters passphrase is used in combination with Password-Based Key Derivation Function 2 (PBKDF2) to create a 256-bit PMK. This is used to derive PTK. Same key for all clients in the case of personal networks
In the case of enterprise network, MSK is used, and the key is different for each client. So there is EAP-Exchange that happens before the 4-way-handshake to derive PMK. (We use PMK caching to skip this) (OKC is an extension of PMK Cache where the cache is distributed to all APs on the L2 network)
GMK - Group Master Key
The group master key (GMK) is a 128-bit key at the top of the hierarchy for broadcast and multicast traffic. The AP generates a cryptographic-quality random number. The GMK is not exchanged directly but is used to derive a group temporal key (GTK). The GMK can be regenerated periodically to reduce the risk of being compromised.
Transient / Temporal Keys
PTK - Pairwise Transient Key
To derive PTK, we use the following as input to a PRF (pseudo-random function):
- PMK
- AP Nonce (Anonce) → Random value generated by AP
- STA Nonce (Snonce) → Random value generated by STA
- AP MAC address
- STA MAC address
Every time a client associates, a new PTK is generated. The PTK key size depends on whether you use TKIP(512 bits) or AES-CCMP(384 bits). It is used to protect WPA 4WHS and Unicast user data.
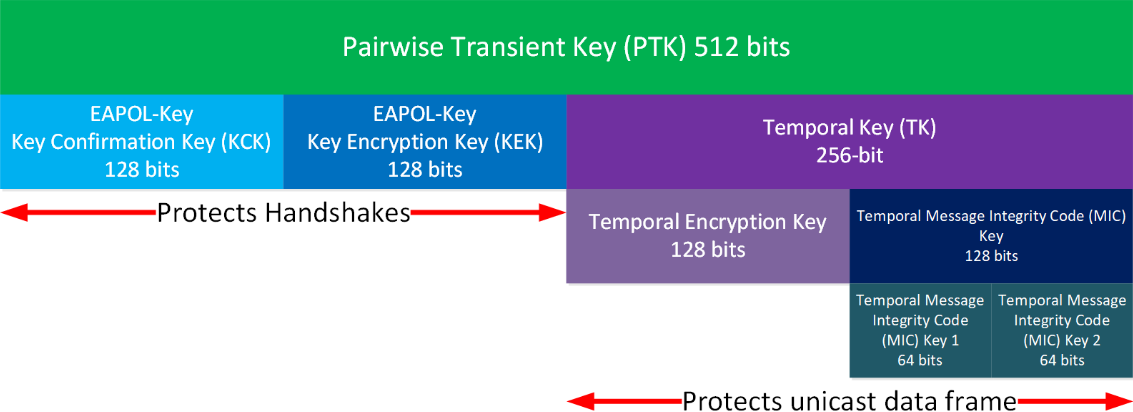
PTK - Pairwise Transient Key - TKIP
This PTK is used to protect handshakes (EAPOL frames) and user data.
Confirmation Key/ Message Integrity Code (MIC) are used to check integrity of the frames.
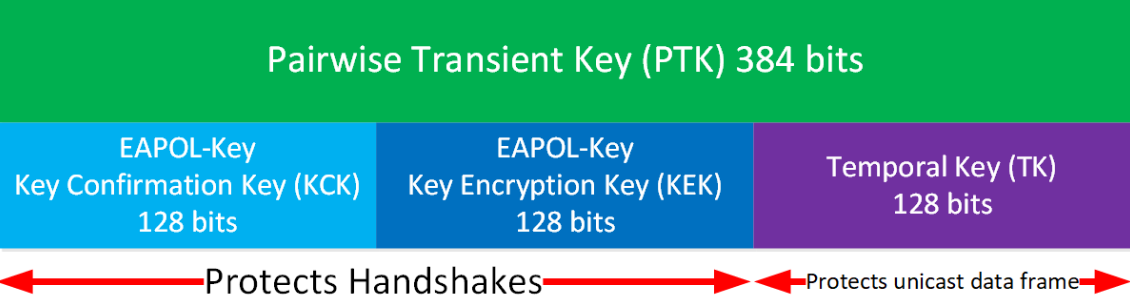
PTK - Pairwise Transient Key - AES-CCMP
AES uses a more robust and modern cryptographic algorithm than TKIP and requires fewer keys and bits. The TK is used for both encryption and integrity checks of MSDUs. The other parts are explained in the image
Group Temporal Key (GTK)
The GTK is derived from the GMK (which is derived using random number) using a PRF and protects all broadcast and multicast traffic between the AP and wireless clients associated with the AP. All wireless clients use the same GTK. During the WPA 4-way handshake, the GTK is sent from the AP to the wireless client. When the AP renews the GTK, it uses a group key handshake called a 2-way handshake. The 2-way handshake is encrypted and does not show up in Wireshark as EAPOL packets. You need to decrypt the packet using passowrd:ssid of the network.
Group Temporal Key (GTK) - TKIP
GTK is divided into encyption key and MIC key
Group Temporal Key (GTK) - AES-CCMP
Similar to the pairwise keys, AES-CCMP uses a single key for encryption and integrity. This key protects broadcast and multicast MSDU frames.
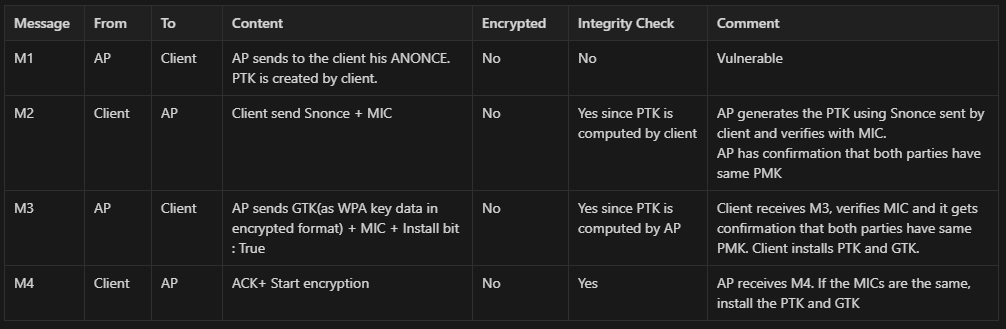
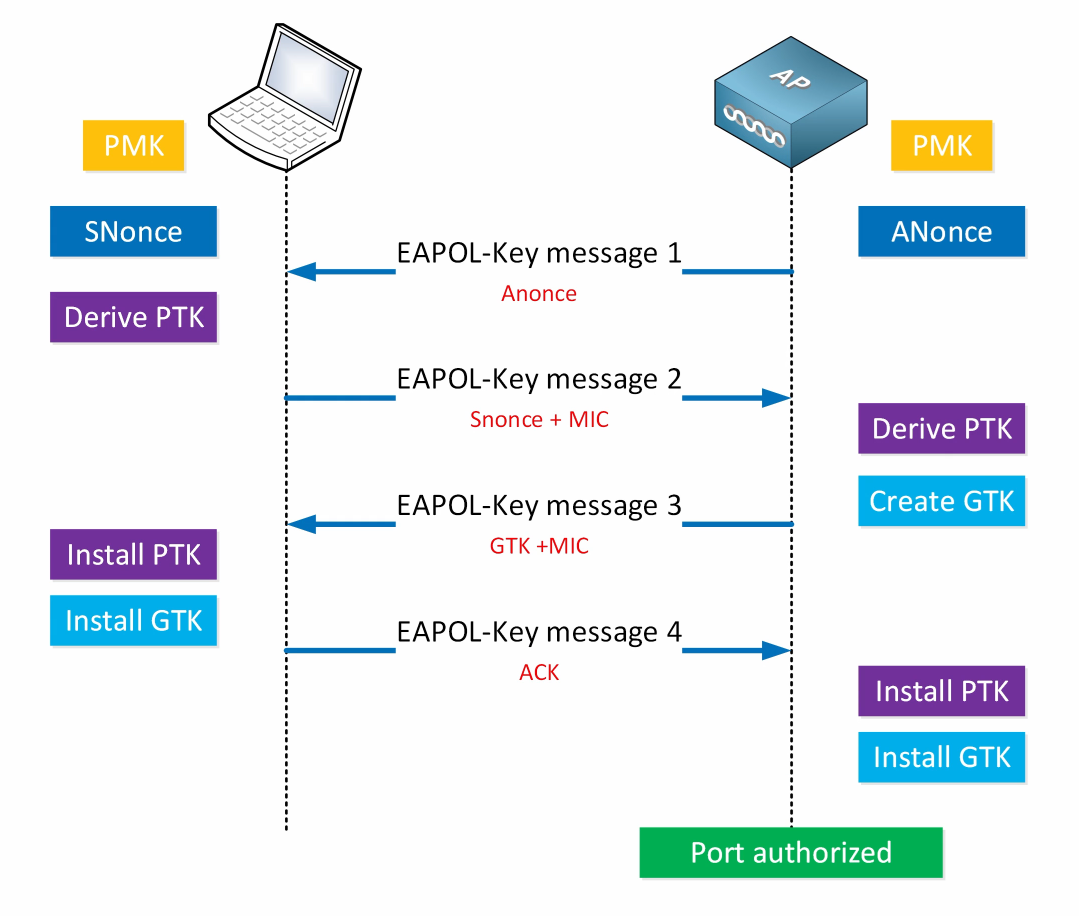
4-Way Handshake Process
The exchange happens through 4 messages usually referred to as M1, M2, M3, M4.
M1, M2 is used to exchange PTK and M3, M4 is used to exchange GTK.
Table
| Message | From | To | Content | Encrypted | Integrity Check | Comment | | ------- | ------ | ------ | ---------------------------------------------------------------------------- | --------- | ----------------------------------- | --------------------------------------------------------------------------------------------------------------------------- | | M1 | AP | Client | AP sends to the client his ANONCE. PTK is created by client. | No | No | Vulnerable | | M2 | Client | AP | Client send Snonce + MIC | No | Yes since PTK is computed by client | AP generates the PTK using Snonce sent by client and verifies with MIC. AP has confirmation that both parties have same PMK | | M3 | AP | Client | AP sends GTK(as WPA key data in encrypted format) + MIC + Install bit : True | No | Yes since PTK is computed by AP | Client receives M3, verifies MIC and it gets confirmation that both parties have same PMK. Client installs PTK and GTK. | | M4 | Client | AP | ACK+ Start encryption | No | Yes | AP receives M4. If the MICs are the same, install the PTK and GTK | undefinedSample 4WHS: https://www.cloudshark.org/captures/d184e6eb5939
https://networklessons.com/cisco/ccnp-encor-350-401/introduction-to-wpa-key-hierarchy
https://networklessons.com/cisco/ccnp-encor-350-401/wpa-and-wpa2-4-way-handshake
https://www.wifi-professionals.com/2019/01/4-way-handshake
IEEE 802.11i-2004 standard
 - TKIP)
 - AES-CCMP)